


USSD/MMI Fix

Description de USSD/MMI Fix
This App will protect you against the remote execution of MMI and USSD codes (from browser links). A recently discovered vulnerability uses Samsung MMI codes and can wipe your device. Apart from that this exploit can be used on malicious web pages to block your SIM card. Since the data wipe is confirmed only for Samsung phones, the SIM blocking MMI command can be executed on many other phones (including HTCs).
Please follow the installation instructions below:
1. Check if your phone is vulnerable.Open your browser and navigate to:http://goo.gl/sRHFC(or scan the barcode at the header of the page).
2. If your phone is vulnerable you will see your IMEI number displayed. (*#06# is not an IMEI number!).
This means that service MMI commands can be executed on your phone, when you visit a malicious web page. The MMI commands are service commands, and if you see the IMEI it doesn't mean that your phone is vulnerable to the Samsungs data wipe vulnerability. Still everyone can execute MMI commands on your phone asking you to open a remote web page URL.
3. If DON'T see the IMEI number, you are safe and you don't need this app :)
4. If you see a popup with your IMEI number, then install this app from Google Play (click on install button on the the left).
5. Once you install the app navigate again to:http://goo.gl/sRHFC(or scan the barcode at the header of the page).
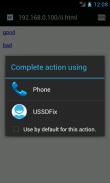
6. Your phone will ask you how to complete the action. Choose USSDFix and mark it as default for this action.
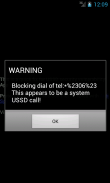
7. You will see a notification that your phone tries to open a page that contains a USSD call and will block it.
8. Your phone is safe now !
NOTE: The app uses a hidden launcher and will not appear in the list of the other apps on your phone desktop. If you want to remove the program, please navigate to Settings / Manage Applications and then remove "USSDfix" app.
Keywords: USSD, security, vulnerability, patch, Notel links, tel link, Android, dirty USSD code, DirtyUssdCode, ekoparty, galaxy, galaxy s III, GalaxySIii, mobilepostcross, Ravi Borgaonkar, RaviBorgaonkar, samsung, security conference, SecurityConference, touchwiz, USSD, USSD code, UssdCode


























